A malware is a threat that affects us all and that is increasing exponentially. In recent years, the malware we face is becoming more sophisticated, because cybercriminals want, first, we do not know who is responsible for creating a malware sample and the second, and essentially, we don’t know what the techniques are used by malware to get into our system and achieve its ultimate goal.
This is what is known as elusive malware, which, when it enters a system, the first thing is to recognize the environment to see if it can run safely. That danger is a virtual machine or sandbox ultimately an environment analysis, which can run and analyze malware without risk.
Given this elusive malware, we have created a tool called Malware Deception, which simulates an environment for the sample analysis not run and also all calls made by the malware to the system to recognize the environment are recorded.
The tool is then able to detect the elusive malware and also have not perform their ultimate goal.
Deception is a tool malware protection throughout the system with precise handling that is implemented in seconds and is very easy to manage. Resource consumption (CPU, memory and disk) system is very low.
In addition, you do not need constant updates, you can operate as a standalone tool requires no special privileges to run, because it works in user mode and the rate of false positives low to nonexistent
Well, now let’s see how this tool works.
The first thing we do is get off the Pafish tool, which is a demonstration tool that uses various techniques to detect sandboxes and analysis environments in the same way that families of malware. We downloaded it from the following link (https://github.com/a0rtega/pafish/archive/v0.5.8.zip)
Unzip the downloaded file and run the executable named pafish.
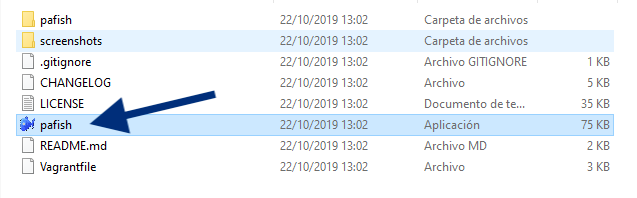
It will start running and should go something like the following image. Most functions should be green meaning that we are in a normal environment.
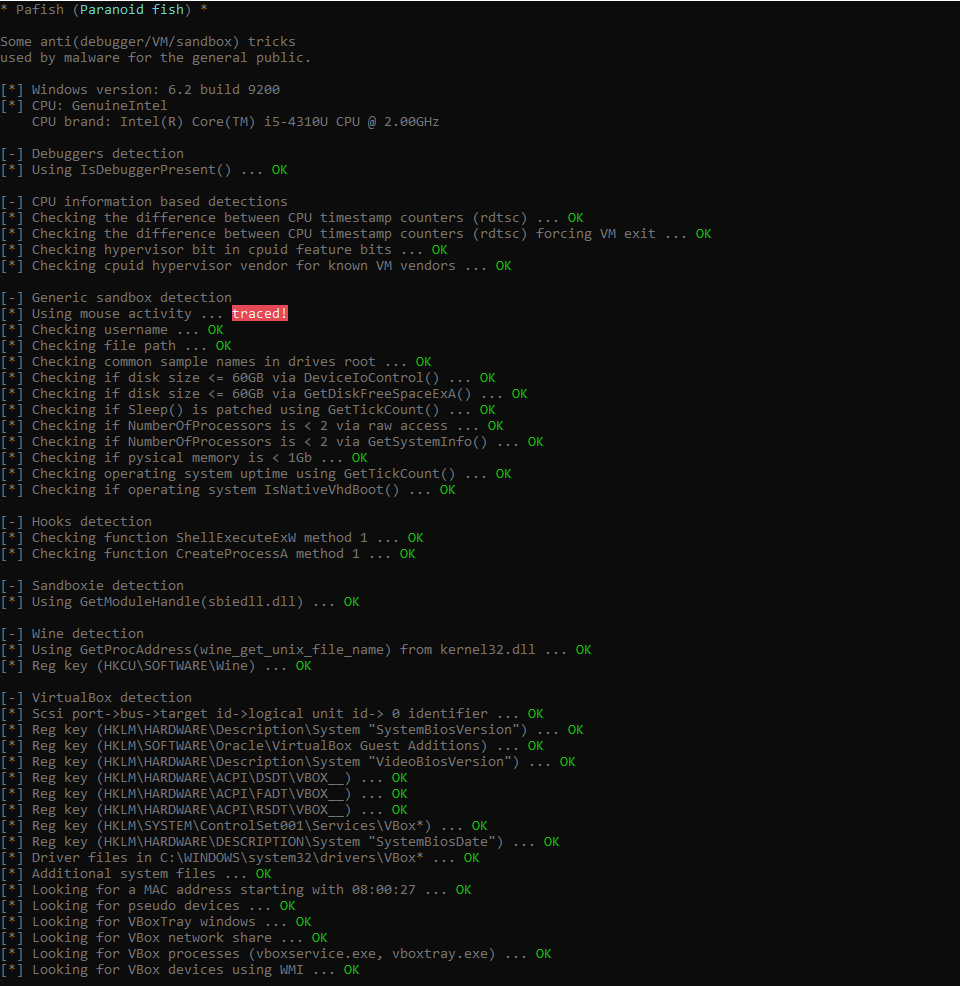
What we have done is to simulate the calls that would make the system to recognize malware and, in this case, appears as a normal environment and not as an analysis environment.
Now we will explain how to install Malware Deception tool on a Windows computer. Malware Deception is compatible with Windows 7 and later systems in both versions of 32-bit and 64-bit.
First of all, we downloaded the tool the link below. The version that we will download expires at the end of 2019. Early next year we will draw a new version.
Then we just have to double-click the executable we’ve downloaded, I installed. Once we installed, an icon appears in the Windows bar like the following image.
![]()
After installing the tool, let’s run Pafish again, but now with Malware Deception installed and running.
As we see the results are quite different from those obtained without the installed Deception Malware. Now all calls to system functions wondered about the environment appear in red, it seems that we are in an environment analysis.
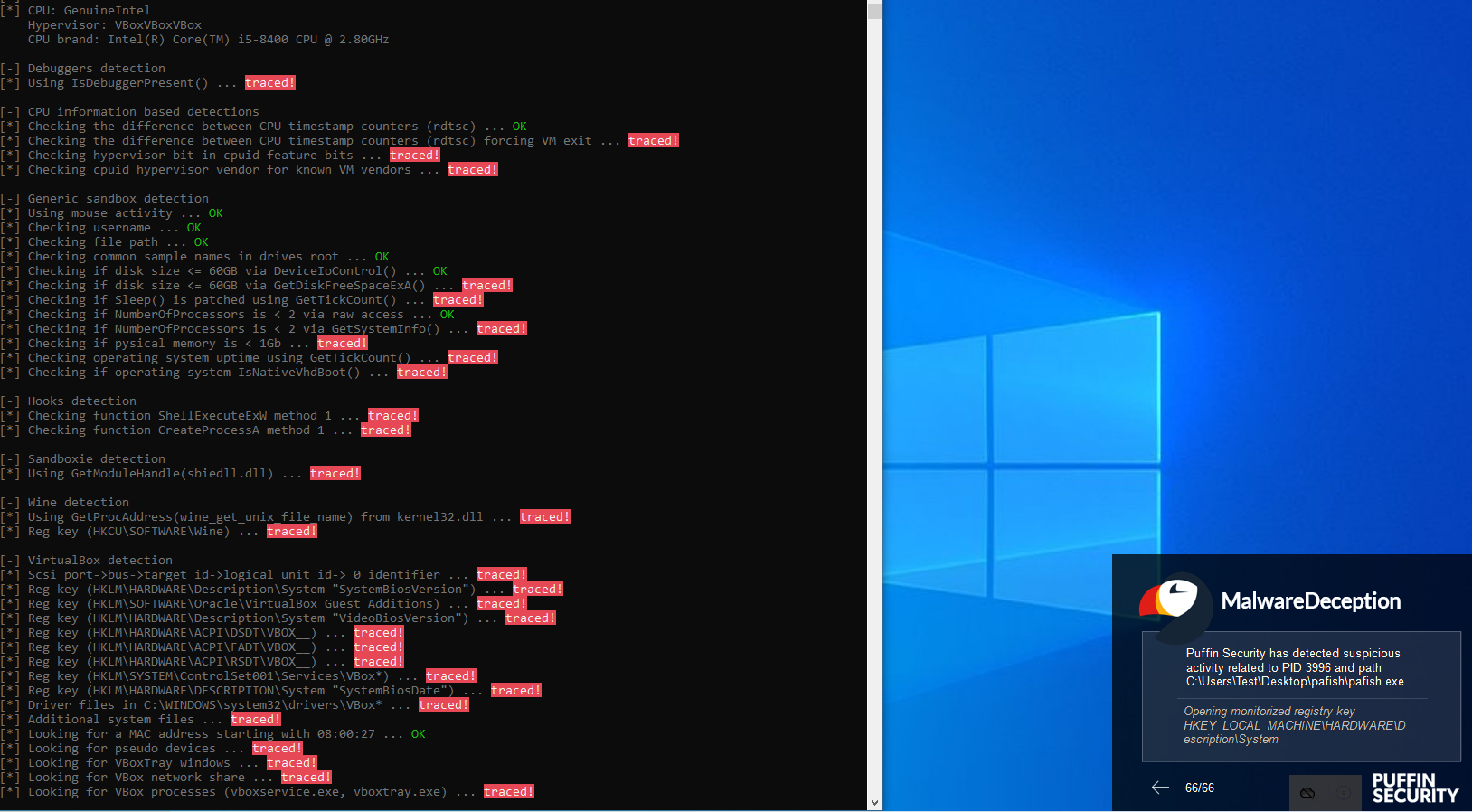
Also, when it was running pafish, each time this was a consultation system was a window warning that a program was recognizing the environment.
Therefore, it has been successfully simulated environment analysis, recorded all system calls made by the executable.
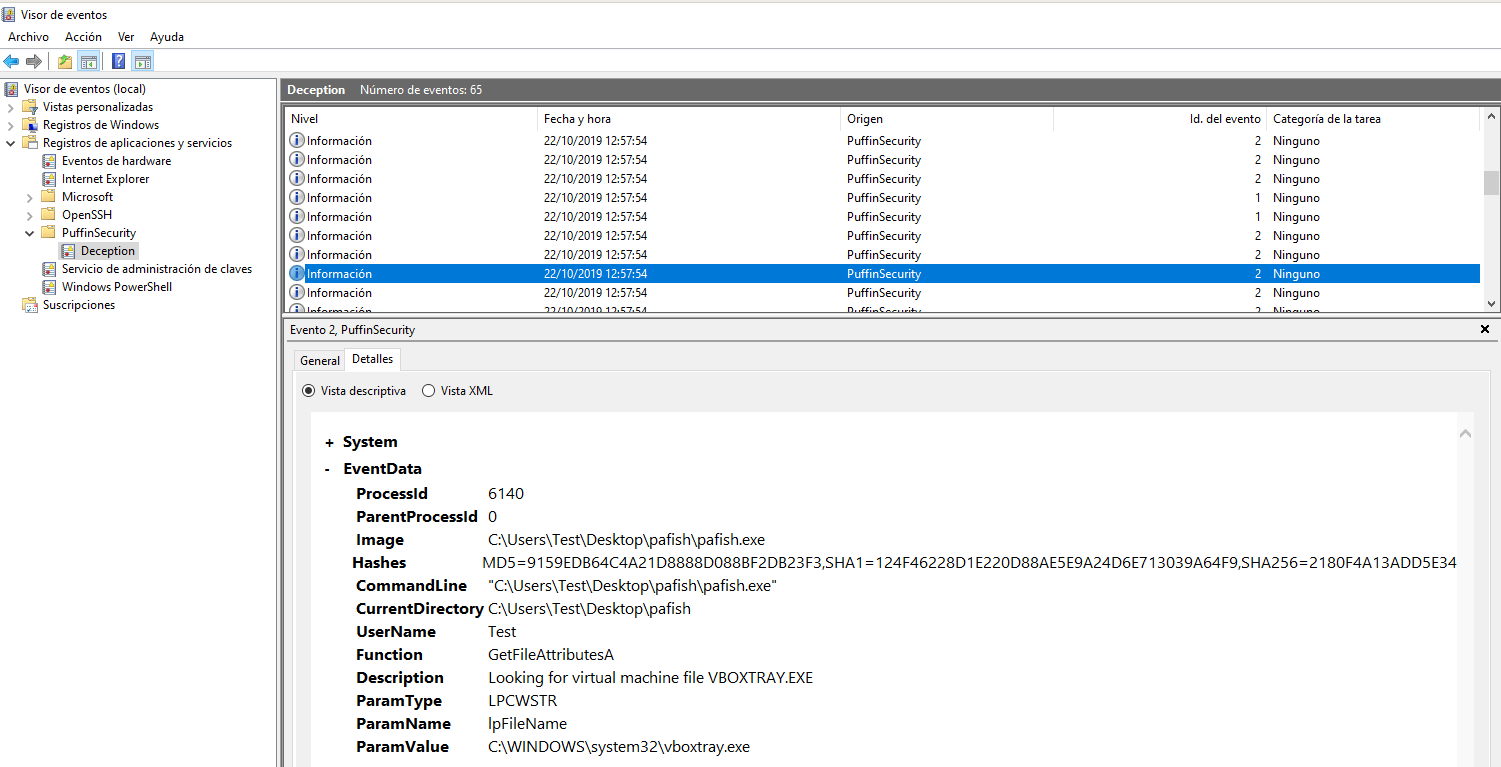
To view all system calls there been making the executable should go to the Windows event viewer. We sought Event Viewer in the search for Windows and open it.
Then select the event log PuffinSecurity as shown in the following image and browse all the different events that have been generated in which the different calls that has been making the program Pafish shown.
And that’s how it works the installed Malware Deception. In the next one we will see how to integrate it with MDR.
References:
https://github.com/psaneme/Kung-Fu-Malware
At Puffin Security, we use the ELITE SECURITY CONSULTING methodology so you can rest assured that your organization will have the highest level of security.
Complete the form, and we’ll be in touch as soon as possible





